Default Encryption
The Virgil E3Kit's default encryption provides true end-to-end encryption and data signature for one or multiple users.
Before you begin
Be sure to implement the following:
- Sample backend or JWT generation on your server side
- Set up your client side with E3Kit
- User authentication functionality
Sign and encrypt data
We encrypt data to hide the message's real content from other parties. But a recipient also needs to be sure that a third party has not modified the message's content and that the message actually came from the expected, authorized sender. So, in addition to encrypting message data for data security, E3Kit uses digital signatures to verify data integrity.
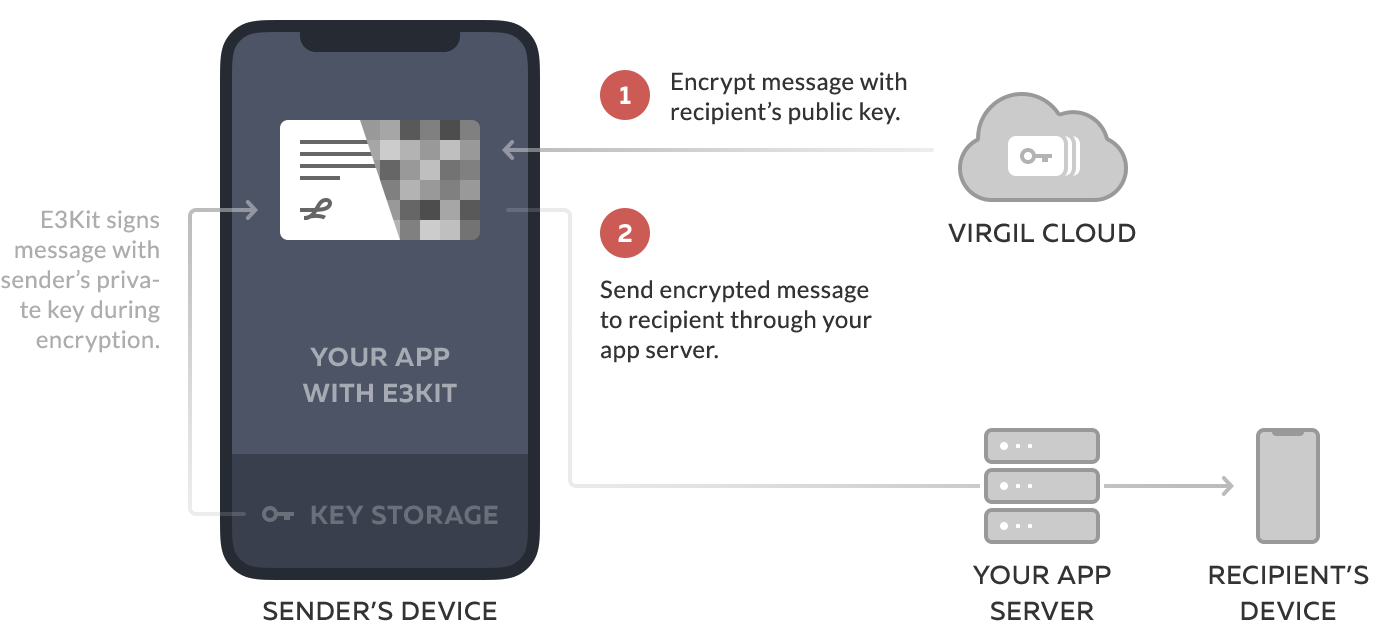
authEncrypt method encrypts the message for recipients' public keys and signs the data with the sender's private key.
The findUsersResult parameter is an array of the recipients' Cards (which contain the public keys of the recipients). In order to retrieve the users' Cards using their identities and generate this array, you'll need to use the findUsers method.
// Listener for findUsers
OnResultListener<FindUsersResult> findUsersListener =
new OnResultListener<FindUsersResult>() {
@Override public void onSuccess(FindUsersResult findUsersResult) {
String text = "I was text but became byte array";
Data data = new Data(text.getBytes());
// Encrypt data using user public keys
Data encryptedData = eThree.authEncrypt(data, findUsersResult);
// Encrypt message using user public keys
String encryptedText = eThree.authEncrypt(text, findUsersResult);
}
@Override public void onError(@NotNull Throwable throwable) {
}
};
// Lookup destination user public keys
List<String> identities = new ArrayList<>(3);
identities.add("userUID1");
identities.add("userUID2");
identities.add("userUID3");
ethree.findUsers(identities).addCallback(findUsersListener);If you want to fully end-to-end encrypt data only for themselves for secure storing on Clouds, don't add the list of public keys (e.g., eThree.authEncrypt('message')).
Encrypted for sender by default. The encrypt method already uses the sender's public key for encryption. Including it again will cause an exception.
Multiple recipients: one ciphertext. Even if a message is sent to multiple recipients, the resulting ciphertext (or encrypted data) will be a single blob/string that all users in the recipient list can decrypt.
Decrypt and verify data
Now let's decrypt the data, then verify that they came from the correct, expected sender.
authDecrypt method decrypts the data using the recipient's private key (remember that the sender looked up the recipient's public key and encrypted the message so that only the recipient's corresponding private key could decrypt the message).
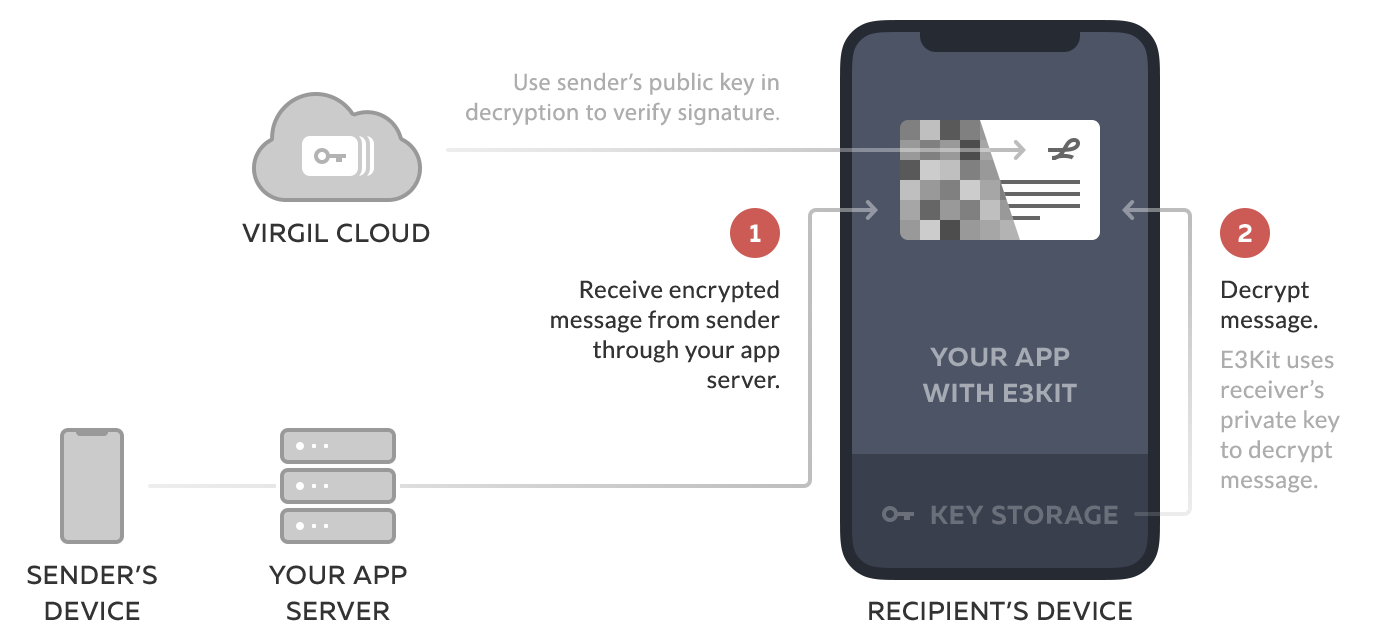
It also verifies the authenticity of the decrypted data with the senderCard parameter, by confirming that the public key on the message signature is the public key of the expected sender. If the senderCard is not specified, method uses the recipient's public key for verification.
Note that the decrypt method from E3Kit version earlier than 0.8.0 is not compatible with the version 0.8.0+ authEncrypt method.
// Listener for findUsers
OnResultListener<Card> findUsersListener =
new OnResultListener<Card>() {
@Override public void onSuccess(Card senderCard) {
// Decrypt data and verify if it was really written by Bob
Data decryptedData = eThree.authDecrypt(encryptedData, senderCard);
// Decrypt text and verify if it was really written by Bob
String decryptedText = eThree.authDecrypt(encryptedText, senderCard);
}
@Override public void onError(@NotNull Throwable throwable) {
// Error handling
}
};
// Lookup destination user public keys
ethree.findUser("bobUID").addCallback(findUsersListener);Limitations
No automatic access to history for new users
While Basic Encryption accepts multiple public keys to encrypt data for multiple users, all the data will need to be re-encrypted should a new user join and wish to have access to the previously encrypted data. For a method that allows new users to join and instantly have access to previously encrypted data (eg. message history), see our Group Encryption method.
No Perfect Forward Secrecy
E3Kit provides a more secure method that implements the Double Ratchet algorithm to accomplish Perfect Forward Secrecy and post-compromise security for one-to-one communication only. See our Double Ratchet Encryption method.