End-to-End Encryption Concept
End-to-end encryption is intended to prevent data being read or modified by anyone but the sender and recipient(s). The messages are encrypted by the sender and decrypted by the recipient locally on their device. Any cloud storage providers or other third parties that transmit or store the data between the sender and recipient handle the data as they normally would. However, it remains encrypted and they do not have a way to decrypt and see the plaintext data under any circumstances.
E3Kit uses asymmetric encryption, meaning that a private & public key is generated for each user or endpoint to secure data in a truly end-to-end fashion.
- The public key is published to Virgil Cards Service, hosted on the Virgil Cloud. When a user want to send a message to another user or group of users, the Virgil E3Kit SDK uses the recipient's public key to encrypt the message data in a way that only the recipient's corresponding private key can decrypt it.
- The private key is kept on the end-user's device, enabling the user and only the user to decrypt any messages or data that other users sent to them. It's similar to the relationship between a public mailing address and a private mailbox. You look up someone's address to send them a letter, but only they can unlock their mailbox to open and read the letter.
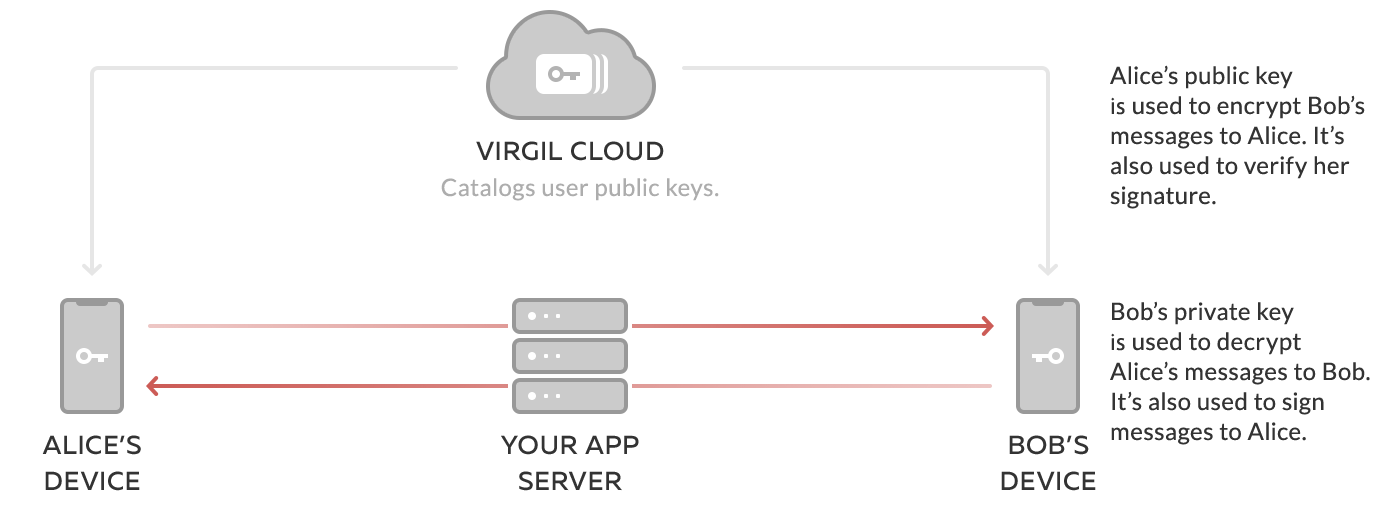
The address book (Virgil Cards Service), mailing address (public key) and mailbox key (private key) are related to each other, but can't be traced to each other in any way that would compromise the security of the system.
This setup enables users to encrypt a message on their phone or computer, send it over the Internet to a recipient without any chance of another party reading it in transit or on the server, and have it be decrypted only by the recipient on their phone or computer. This all works seamlessly for the end users and can be implemented easily by the average developer using E3Kit.