Post-Compromise Security
Post-compromise security (PCS) is the protection of users' data after the encryption key has been compromised. PCS can be provided by implementing the following features at the server:
Seamless key rotation
Retiring the old encryption key and replacing it with a new one. Keys should be able to be rotated while the app is running and they can be rotated both proactively or if there is a data breach.
Invalidation of stolen data
Data cannot be decrypted without the cooperation of the crypto server, rendering any stolen data in a database useless.
Zero Knowledge proof
Crypto service proves all operations were performed using its private key.
Withstanding both online and offline attacks
Strict rate limiting per-user; to make a password attempt, the private keys of both the application and the crypto service are required.
Key rotation and data invalidation
Keys rotation helps you render a stolen database useless without any inconvenience to the end users. This section shows how Keys Rotation works.
If your database has been compromised, or as needed during routine maintenance, the Service Provider may engage in a key rotation protocol to rotate secret keys so that they are distributed identically as freshly generated keys. Then, the Service Provider locally runs the update algorithm on each record to validate the new keys.
Note that the update is done without knowing user passwords. In the key rotation protocol, the PHE Service generates a random update token and sends it to the Service Provider. The latter updates its Secret Key, and the PHE Server updates its Secret Key.
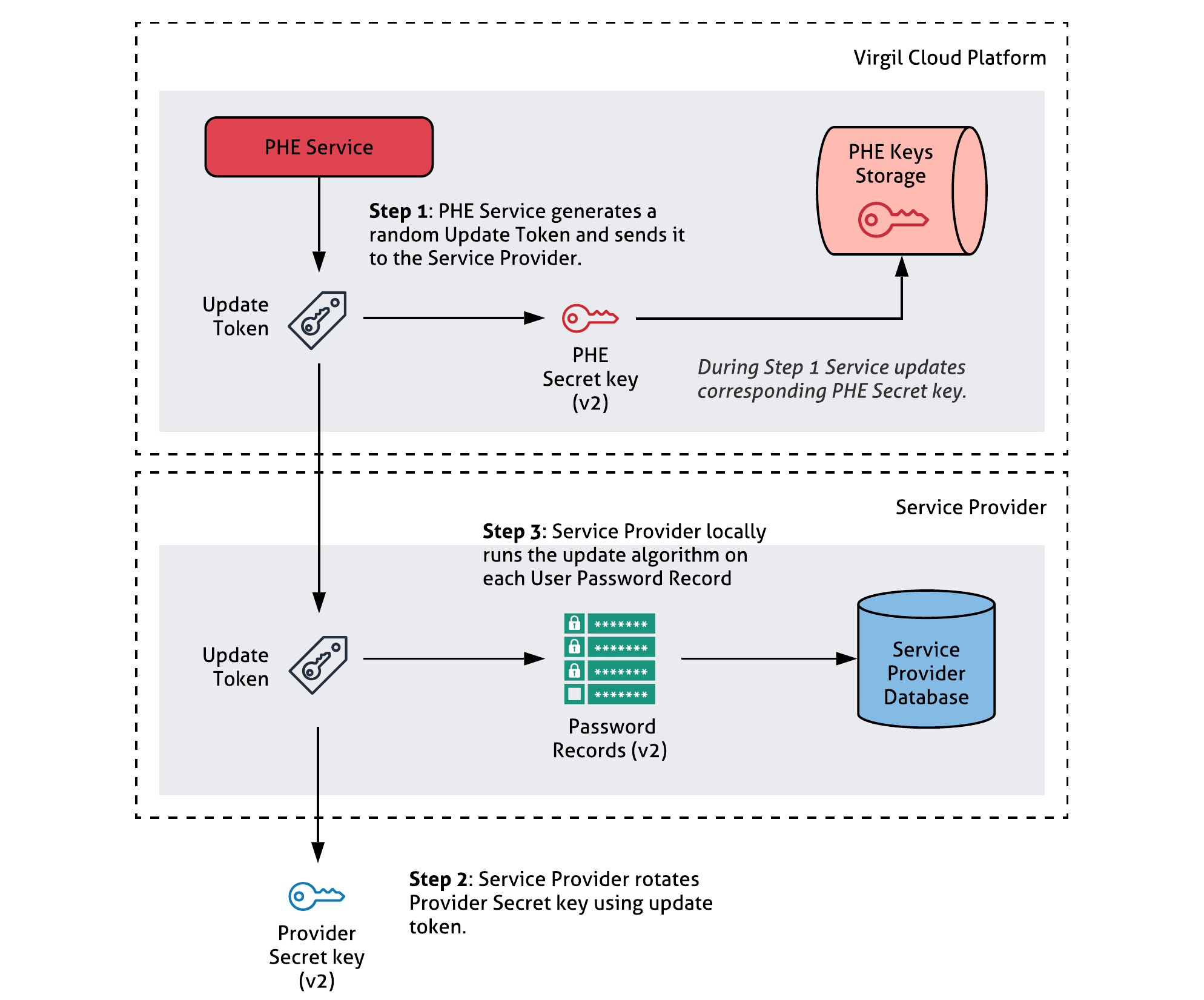
Approach advantages:
- The Service Provider can rotate secret keys and users’ password records in database at any time
- The key-rotation mechanism is invisible to the end users.
- The App Server can locally update end user records without interacting with the PHE Service or the end users.